SNMP
Intro
Simple Network Management Protocol(SNMP) is used to monitor network devices. It can also be used to configure and change settings remotely.
It is a client-server based architecture where there is a SNMP manager acts like a client and SNMP agents act like a server. SNMP agents are installed on all the devices that needs to be monitored/configured such as routers, switches or computers. SNMP agents are responsible for translating internal device information into SNMP format. They maintain MIB(Management Information Base) for this purpose. They listen on UDP port 161 for SNMP requests. SNMP requests can either be simple query or configuration change request. The SNMP agents can also be configured to send “TRAPS” to certain manager on UDP port 162. These “traps” are sent by the agent(server) to the manager(client) when certain events occur without explicit request from the manager.
Note: Although, it is general practice to have a dedicated machine for SNMP manager which sends the SNMP requests, it doesn’t mean that any other device on the network cannot send the request.
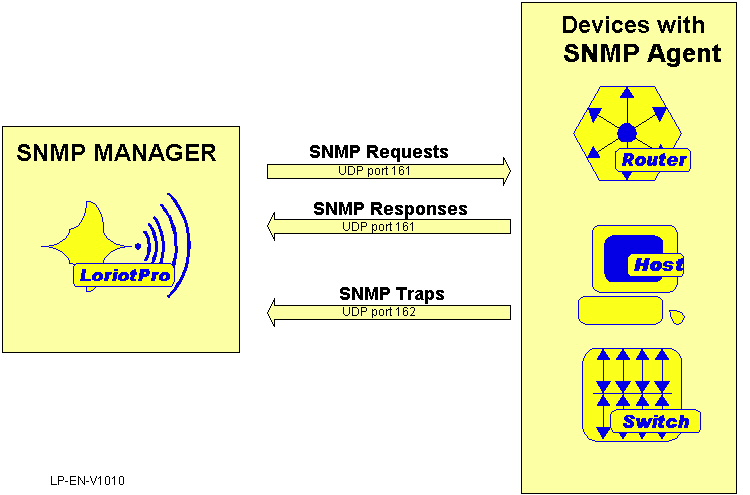
To exchange information between the client and server, SNMP uses MIB and OIDs.
MIB(Management Information Base)
It is a text file with .mib extension which contains information regarding all queryable SNMP objects in a standardized tree hierarchy format. It contains at least one OID along with other meta-data such as type, access rights and description.
OID(Object Identifier)
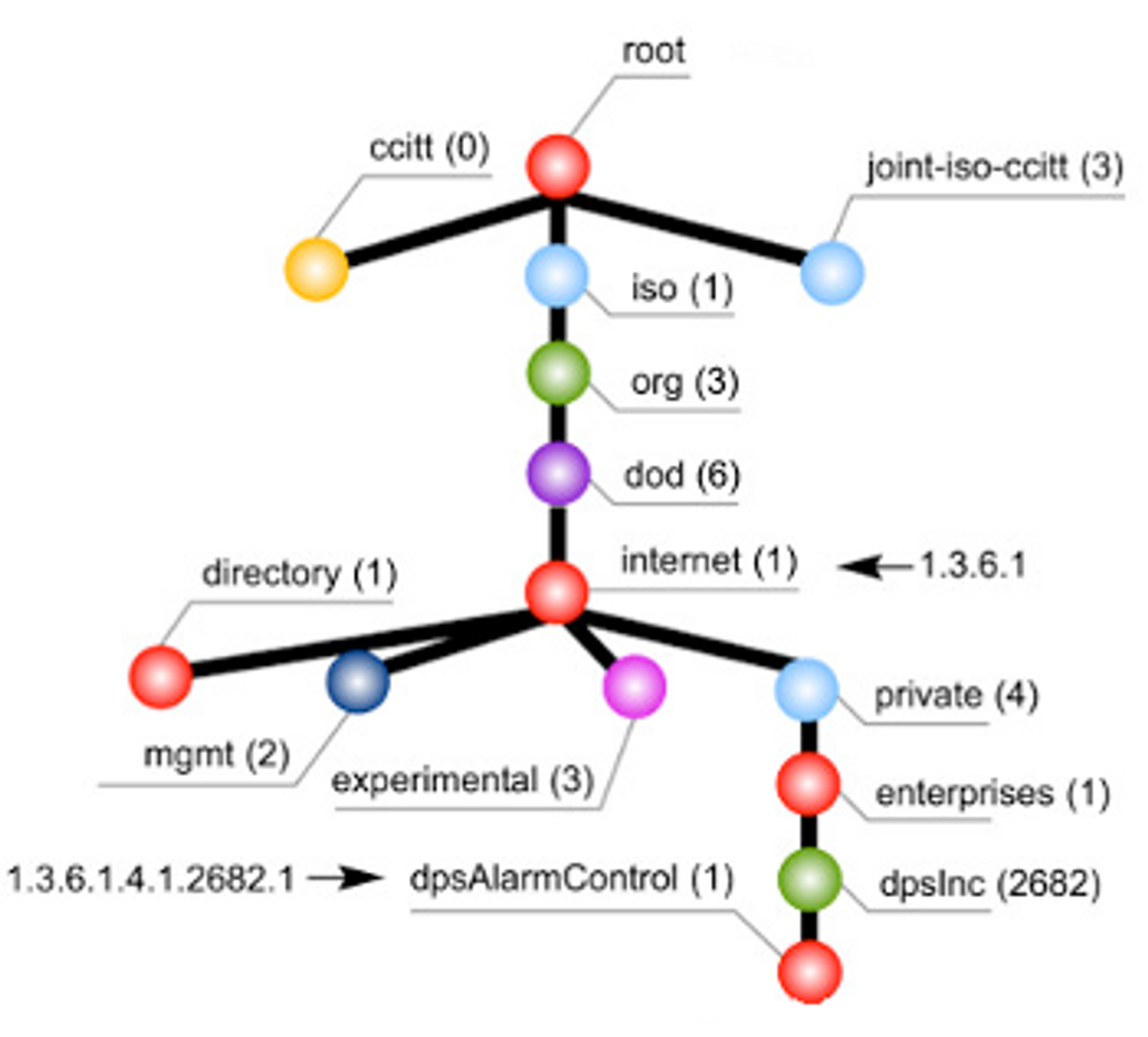
Similar to how domain hierarchy is maintained for domain name resolution, hierarchy of objects are maintained in SNMP. Each object might represent certain parameter of the monitored device such as CPU, memory, etc. or they might contain nothing except references to those below them. The OIDs consist of integers and are usually concatenated by dot notation. There are already a set of global OIDs managed by various organizations such as ISO, IANA. The global OID hierarchy can be found here. If we want to add certain parameter to the global OID hierarchy, we can submit request via forms to the relevant standard organizations(IANA, ISO), which will be reviewed and if approved gets added globally.
However, if we just want to use our own OID private to our organization, they are done under 1.3.6.1.4.1 which is allocated for internet private enterprises. It is recommended to register with IANA which will allocate a unique OID for our organization to prevent conflicts and ensure that OIDs are unique and interoperable when interacting with other SNMP-based systems. However, it is possible to use unregistered private OIDs under 1.3.6.1.4.1 sub tree but it will only be valid within the scope of organization’s network.
SNMP versions
SNMP protocol has evolved over time and SNMPv3 is the latest version available.
SNMPv1
They have the provision for retrieving information, configuration of devices and traps. However, they have no built-in authentication mechanism. On top of that, it also doesn’t support encryption, which can easily lead to the violation of privacy.
SNMPv2
There were two different versions of SNMP2 protocol: SNMPv2c(community-based) and SNMPv2u(User based). However, due to interoperability issues with SNMPv2u, SNMPv2c is the standard SNMPv2 today. In this version, “community string” is used which acts like a passcode i.e. only those requests that have this pass code are allowed to view the requested data. However, the issue of communication being in cleartext is still present which means the requests can be intercepted to find out the community string.
SNMPv3
More secure compared to the previous versions. It allows security features such as authentication(username and password) and encrypted transmission of data. But this also increases the complexity which is why SNMP2 is still in use.
Configuration
The SNMP agent configuration file is located at /etc/snmp/snmpd.conf.
sysLocation Sitting on the Dock of the Bay
sysContact Me <me@example.org>
sysServices 72
master agentx
agentaddress 127.0.0.1,[::1]
view systemonly included .1.3.6.1.2.1.1
view systemonly included .1.3.6.1.2.1.25.1
rocommunity public default -V systemonly
rocommunity6 public default -V systemonly
rouser authPrivUser authpriv -V systemonly
Dangerous Settings
Some dangerous settings that the administrator can make with SNMP are:
| Settings | Description |
|---|---|
| rwuser noauth | Provides access to the full OID tree without authentication. |
| rwcommunity |
Provides access to the full OID tree regardless of where the requests were sent from. |
| rwcommunity6 |
Same access as with rwcommunity with the difference of using IPv6. |
Tools
snmpwalk
It can be used to query the OIDs with their information. It performs a series of SNMP GETNEXT request(retrieves next object in MIB hierarchy) under the hood. SNMP Manager also uses this command to gather information from various devices in the network.
snmpwalk -v2c -c {community_string} {agent_IP_hostname} [OID]
-v is used to specify the version of SNMP protocol to use (1|2c|3)
-c is used to specify the community string in case of v1 or v2c
-P specify the port number to use for SNMP connection
-t specify timeout in seconds(default value 1 second)
-r specify number of retries(default value 5)
The timeout -t and retry -r option parameters are applied to each individual SNMP GETNEXT command that are called underneath.
1.3.6.1.2 OID has been allocated for management. 1.3.6.1.2.1 has been allocated for MIB related parameters. OIDs under this sub tree provides information present in the snmp configurations such as sysContact - 1.3.6.1.2.1.1.4, sysLocation - 1.3.6.1.2.1.1.6, sysServices - 1.3.6.1.2.1.1.7.
onesixtyone
Community strings are specific to agents and generally named with the hostname of the host. onesixtyone can be used to brute-force community string with the SecLists wordlists.
onesixtyone -c /opt/useful/SecLists/Discovery/SNMP/snmp.txt {agent_IP}
braa
Once the community string is identified, braa can be used to get the information regarding OIDs supported.
braa <community string>@<IP>:.1.3.6.*