Mail: SMTP
Intro
SMTP(Simple Mail Transfer Protocol) is a protocol for sending emails which can be used between an email client and a mail server or between two mail servers where one of the servers essentially act as client.
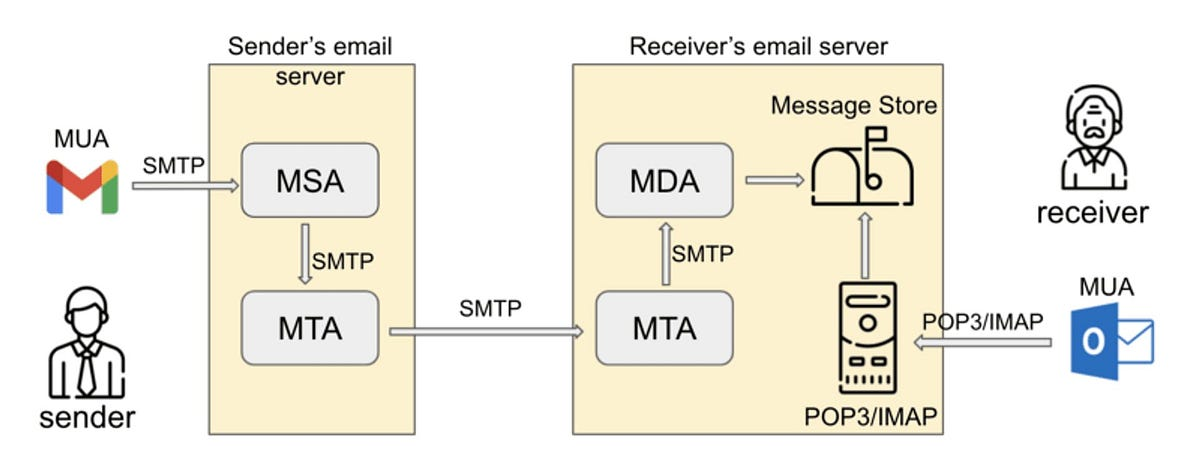
The SMTP client, also known as Mail User Agent (MUA), converts it into a header and a body and uploads both to the SMTP server. This has a so-called Mail Transfer Agent (MTA), the software basis for sending and receiving e-mails. The MTA checks the e-mail for size and spam and then stores it. To relieve the MTA, it is occasionally preceded by a Mail Submission Agent (MSA), which checks the validity, i.e., the origin of the e-mail. This MSA is also called Relay server.
On arrival at the destination SMTP server, the data packets are reassembled to form a complete e-mail. From there, the Mail delivery agent (MDA) transfers it to the recipient’s mailbox.
Ports and Authentication
The standard port used by SMTP server is 25 which does not require any form of authentication and the communication is also in plain text.
To make it more secure, Extended SMTP(ESMTP) has been developed which enables TLS to make the communication encrypted by sending STARTTLS command right after EHLO(Extended HELO) command. For this purpose, the SMTP server can be configured to listen on a different port(not 25). Nowadays, when people refer to SMTP, they usually mean ESMTP.
Even with this approach, there is no sender verification. So, newer SMTP servers listen on port 587 for authenticated users. Username and password is sent for authentication and only after the sender along with the receiver email addresses have been verified, email is sent to receiver mail server.
Configuration
Sendmail is one of the oldest SMTP servers but due to its complexity and security concerns, postfix mail server was developed. In most linux systems, postfix is commonly used as the default MTA.
The configuration file for postfix mail server is located at /etc/postfix/main.cf. Many different settings can be set up on this file.
smtpd_banner = ESMTP Server
biff = no
append_dot_mydomain = no
readme_directory = no
compatibility_level = 2
smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
myhostname = mail1.mydomain.com
alias_maps = hash:/etc/aliases
alias_database = hash:/etc/aliases
smtp_generic_maps = hash:/etc/postfix/generic
mydestination = $myhostname, localhost
masquerade_domains = $myhostname
mynetworks = 127.0.0.0/8 10.129.0.0/16
mailbox_size_limit = 0
recipient_delimiter = +
smtp_bind_address = 0.0.0.0
inet_protocols = ipv4
smtpd_helo_restrictions = reject_invalid_hostname
home_mailbox = /home/postfix
Dangerous settings
Out of these,
mynetworks = 0.0.0.0/0
setting allows all IP addresses. This enables SMTP server to send fake emails and initialize communication between multiple parties.
Open Relay Attack
An open mail relay is a Simple Mail Transfer Protocol (SMTP) server configured in such a way that it allows anyone on the Internet to send e-mail through it, not just mail destined to or originating from known users. This used to be the default configuration in many mail servers; indeed, it was the way the Internet was initially set up, but open mail relays have become unpopular because of their exploitation by spammers and worms. Many relays were closed, or were placed on blacklists by other servers.
Source: https://en.wikipedia.org/wiki/Open_mail_relay
Nowadays, most SMTP servers mandate authentication. So, this vulnerability is not much popular. However, some internal servers might not enforce them. In such cases, this can be exploited.
Nmap scripts
nmap script smtp-commands can be used to list all possible commands that can be executed on the target SMTP server
sudo nmap {IP} --script smtp-commands -sV -p25
nmap script smtp-open-relay can be used to test if the target SMTP server is open relay or not:
sudo nmap {IP} --script smtp-open relay -p 25
SMTP commands
| Command | Description |
|---|---|
| AUTH PLAIN | AUTH is a service extension used to authenticate the client. |
| HELO | The client logs in with its computer name and thus starts the session(gives a list of commands that can be executed on the server) |
| MAIL FROM | The client names the email sender. |
| RCPT TO | The client names the email recipient. |
| DATA | The client initiates the transmission of the email. |
| RSET | The client aborts the initiated transmission but keeps the connection between client and server. |
| VRFY | The client checks if a mailbox is available for message transfer(might be used to check if the user on the recipient mail server exists or not) |
| EXPN | The client also checks if a mailbox is available for messaging with this command. It is used to find the delivery address of mail aliases. |
| NOOP | The client requests a response from the server to prevent disconnection due to time-out. |
| QUIT | The client terminates the session. |
We can use nc or telnet command to establish SMTP connection with the server. Once the connection has been established, above commands can be sent. Running the SMTP commands returns certain response codes. A list of all SMTP response codes can be found here.
If we do not want to open an interactive SMTP session and simply care about executing the command and getting output, it can be done as:
echo "VRFY myusername" | nc {IP} {port}